Building Multi-Cloud Confidential Computing: The Danger of Cloud and Data Lock-In
Multicloud enablement is one of the most important differentiators over other cloud lock-in confidential vaults. SafeLiShare develops a cloud-agnostic and developer-friendly secure data platform that easily enables uni-party or multi-party data sharing and enforces data custodianship with one click or one command, no matter where your data is and which cloud you are in.
In the context of cloud computing, cloud lock-in (also known as vendor lock-in or data lock-in) refers to the situation where a company or organization becomes dependent on a particular cloud service provider and finds it difficult or costly to switch to another provider or to move to an on-premises solution. This can happen when a company has invested heavily in a provider’s proprietary tools, technologies, or services, making it difficult to migrate to another provider without significant disruption or cost. Cloud lock-in can limit a company’s flexibility, innovation, and ability to negotiate better pricing or terms, and it can also create security and compliance risks.
The real value of adopting multiple clouds won’t be realized until cross-cloud exists to enable secure data sharing across cloud providers and regions.
The recent announcements of Google Confidential Space and Azure Confidential Containers once again validate and support the importance of maintaining privacy, encryption in use, and multi-party data sharing throughout the data pipeline.
This article shares our views on the recent announcements from GCP and Microsoft Azure. SafeLiShare Secure Data Platform supports confidential compute and data assets in AWS, Azure, and GCP. We will go over some of our platform features and benefits to help you answer multi-cloud and agnosticity challenges in confidential computing with a cloud-native and developer-friendly approach.
Confidential Computing on Azure and GCP
ACI (Azure Container Instances) is an Azure service that provides an enterprise the ability to easily deploy containers in Azure. Confidential containers are containers that run in a hardware-backed trusted execution environment (TEE) that provides attestation and isolation capabilities that help realize data and code confidentiality and integrity. Azure recently announced (azure.microsoft.com/en-us/updates/public-preview-confidential-containers-on-aci/) support for confidential containers on ACI using AMD EPYC™ processors with confidential computing capabilities.
Applications that require data and/or code confidentiality can be built using confidential containers on ACI. An example of such an application is where data and code are from multiple parties that do not have a mutual trust relationship. Several such application scenarios are mentioned at techcommunity.microsoft.com/t5/apps-on-azure-blog/announcing-public-preview-of-confidential-containers-on-azure/ba-p/3755623.
Google Confidential Space is a Google service for enabling such sharing applications on Google’s cloud infrastructure (cloud.google.com/blog/products/identity-security/announcing-confidential-space). Confidential Space also uses TEE and is designed to release secrets only to authorized workloads. Examples of confidential data include data with personally identifiable information (PII) or other regulated or sensitive data. Each party sharing data in a Confidential Space retains confidentiality and ownership of its data, thereby enabling mutually distrusting parties to collaborate together. For further details on Confidential Space, refer to cloud.google.com/docs/security/confidential-space
Azure Confidential Containers on ACI and Google Confidential Spaces announcements highlight the need for confidentiality properties for data and applications running on public clouds and in particular data-sharing use cases involving multiple separate and mutually distrusting parties.
This validates SafeLiShare’s vision of sharing use cases and that it is on the right track to empower the ongoing adoption of public cloud computing with data confidentiality without any platform dependency.
Not all data is created equal. Your data can be in any cloud, data pipeline, bucket, data warehouse, data lake, or lakehouse. With ubiquitous security, increased chip-level TEE availability, and viability of #secureenclave technology from Intel® SGX, AMD Secure Encrypted Virtualization (SEV) to AWS Nitro System, SafeLiShare delivers zero trust to a new level of innovation with low code APIs where data confidentiality is preserved and privacy controls are enforced.
Answer Multicloud and Agnosticity Challenges
Many organizations using public cloud services or SaaS store data on multiple clouds, but currently, that data is typically managed and accessed within the context of a single cloud environment. As cloud computing continues to be the main location for data, data and analytics leaders will likely look for ways to bring the data together in a logical, secure, and cohesive manner.
Confidential computing is the next generation of cloud computing where enterprises need continuous access to their data from any cloud at any time, providing globally distributed applications and avoiding dependence on any single cloud service provider. The need can come from regulatory mandates for the use of multiple clouds for resilience, availability, data custodianship, and data sovereignty laws.
In Confidential Computing, besides data assets, there are application programs or code assets for computation and invisible modeling. These global applications operate on a global basis on the edge or in the cloud and may require the use of multiple clouds to meet latency and performance requirements without compromise.
SafeLiShare supports distributed data integration to achieve maximum value of hybrid and multi-cloud computing.
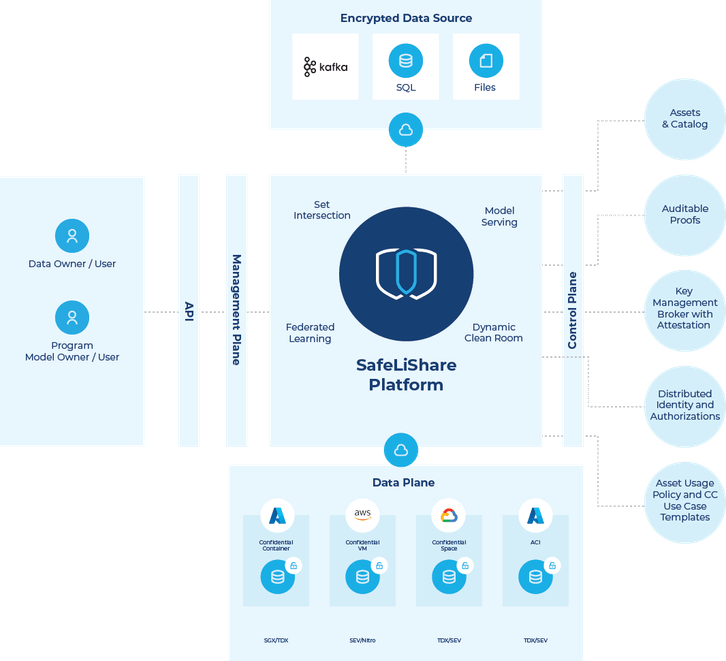
SafeLiShare offers a full confidential computing solution comprising of:
- a control plane that enables distributed authorization for assets, asset discovery, and specification and validation of computations defined over these assets
- the computations are expressed as instances of application templates
- a data plane, where the specified computations are run; and an auditable proof provided where needed that the computation and use of assets happened in a trusted environment
Hybrid, Multi-Cloud Privacy by Design
Significant benefits offered by Safelishare include:
- SafeLiShare allows for easy and secure execution of confidential computing applications, including encrypted clean rooms and computations that combine confidential and non-confidential inputs.
- A variety of application templates provided enable the realization of a number of application scenarios
- Allows developers to focus on application characteristics while the SafeLiShare platform takes care of the underlying confidential computing aspects
- Ease of training developers being introduced to creating confidential applications
- A single unified and user-friendly platform for realizing many application scenarios as opposed to having multiple solutions each supporting a single application scenario
- Different application scenarios are realized using platform features including application templates, asset use policies, and distributed authorization where asset owners maintain full ownership of their raw asset data and associated keys
- Same user interface is supported for Confidential Computing on multiple cloud platforms (Azure, GCP, AWS)
- Enables the creation of applications that can be easily transported.
- Allows enterprises that need confidential workloads on multiple platforms to use a common specification without having to learn multiple different platform details
- Support for use of an alternate data plane, where appropriate, offered by cloud providers to run the specified applications (eg. Azure ACI, Google Confidential Spaces…)
- This platform enables applications to utilize the capabilities of multiple data planes while still maintaining ease of use through Safelishare.
- Support auditable proofs where needed for demonstrating that computations and use of assets happened in a trusted environment
- Support for private cloud deployments
- Utilizes a plugin architecture to incorporate diverse data sources based on requirements, i.e. blob/file storage across clouds and Kafka/SQL services from various providers
- Data can be used in a confidential manner when combined from various sources.
As shown in the above figure, Azure Confidential Containers on Azure Container Instances and Confidential Space can be used as alternate data planes for the SafeliShare solution thus preserving the ease of use and other benefits offered by the SafeLiShare control plane. For more information, on how you can enable confidentiality and privacy as easily as an API call or a command line, schedule an introduction of SafeLiShare’s cloud-agnostic confidential computing at safelishare.com/demo/.
Experience Secure Collaborative Data Sharing Today.
Learn more about how SafeLiShare works
Suggested for you
February 21, 2024
Cloud Data Breach Lifecycle Explained
During the data life cycle, sensitive information may be exposed to vulnerabilities in transfer, storage, and processing activities.

February 21, 2024
Bring Compute to Data
Predicting cloud data egress costs can be a daunting task, often leading to unexpected expenses post-collaboration and inference.

February 21, 2024
Zero Trust and LLM: Better Together
Cloud analytics inference and Zero Trust security principles are synergistic components that significantly enhance data-driven decision-making and cybersecurity resilience.