Secure SaaS data with simple API calls
Secure enclave protects the confidentiality and secrecy of your data when they are not under your control. SafeLiShare wraps SaaS apps using easy APIs and runs them in secure enclaves to alleviate the concern of SaaS data leakage.
- Have concerns about sharing data with cloud services to prevent data leakage
- Process data on behalf of other administrative domains
- Have concerns sharing user private data to partners for selective use
- Need immutable and trusted logs for GDPR and HIPAA compliance etc
Get all traceability and risk control you need on your data in SaaS Mesh
Eliminate Compromise and Data Loss
SafeLiShare can prevent SaaS data access from unauthorized parties and stop growing common attack vector due to the lack of SaaS security measures, such as encryption and policy-driven access controls.
Secure Data Access from Federated Secure Enclaves
Data federation allows data from different departments and organizations to be aggregated a mesh of secure containers. Each contributor retains control of their data, ensuring continued privacy controls without compromise.
Enable Encryption in Use Instantly
With SafeLiShare’s no-code APIs and CLI toolkit, SaaS providers can assure peace of mind for their customers on highly regulated data exposure by encrypting data and application code at all times.
GDPR and HIPAA Compliance Ready Access Logs
Logs generated in a tamper-proof way that can be efficiently verified and flowed into SaaS provider’s management portal in real time and help monitor usage forensic evidence required by regulatory compliance.

“The only secure way to run SaaS applications is to encrypt all of the data on the client side and only send encrypted data to the SaaS app. SafeLiShare provides the fastest integration to enable confidential computing on our SaaS platform.”
Jung-Chen (JC) Lee, Product Manager
Kdan Mobile
People also ask
How can SafeLiShare’s Trusted Execution Environment stop supply chain compromise during data sharing?
Can confidential computing be implemented in all industries to prevent 3rd party supply chain attacks?
How can SafeLiShare’s TEE innovation prevents CSP or SaaS provider
Additional materials
February 21, 2024
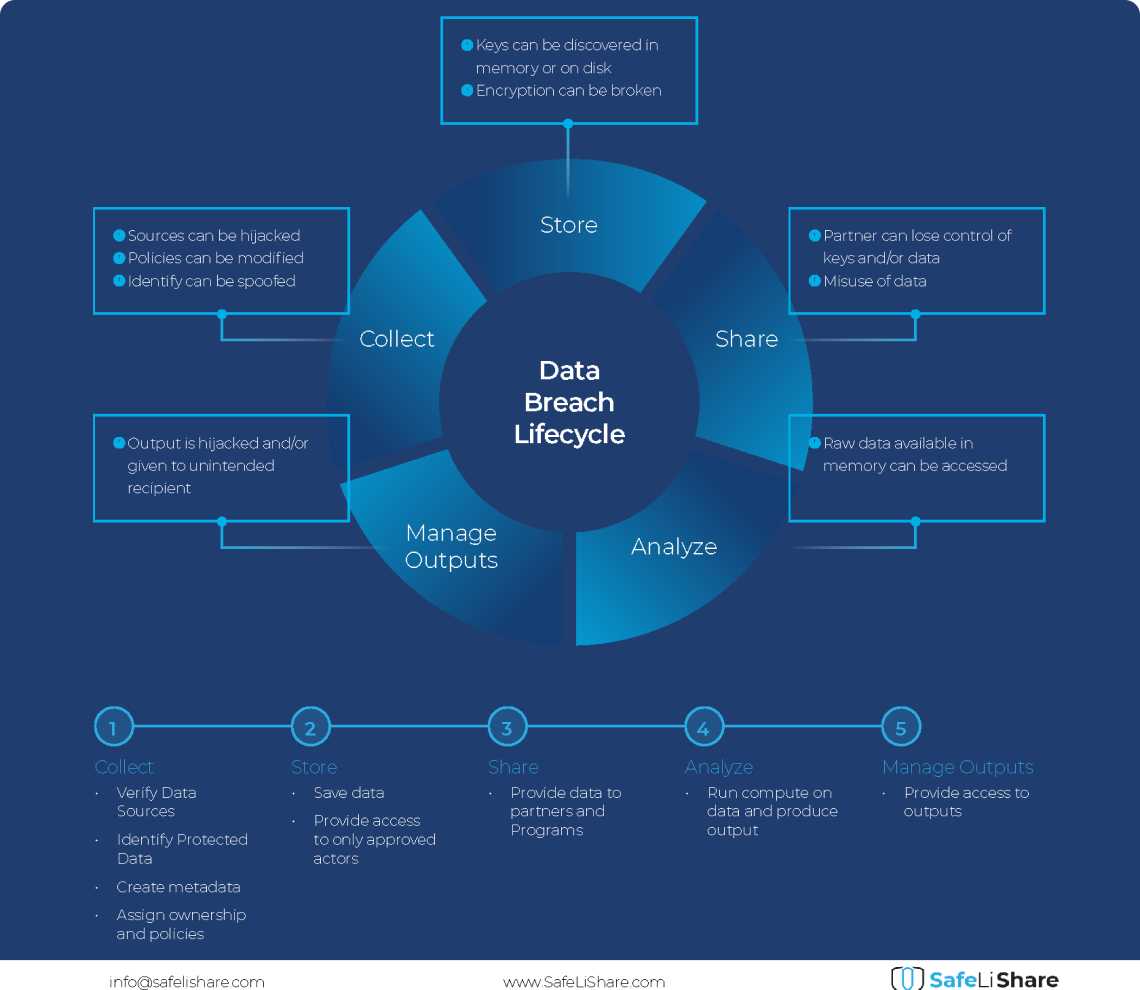
Cloud Data Breach Lifecycle Explained
During the data life cycle, sensitive information may be exposed to vulnerabilities in transfer, storage, and processing activities.

February 21, 2024
Bring Compute to Data
Predicting cloud data egress costs can be a daunting task, often leading to unexpected expenses post-collaboration and inference.

February 21, 2024
Zero Trust and LLM: Better Together
Cloud analytics inference and Zero Trust security principles are synergistic components that significantly enhance data-driven decision-making and cybersecurity resilience.
Experience secure collaborative data sharing today.
Maximize accessibility and monetization of sensitive, regulated, or confidential data without compromise.